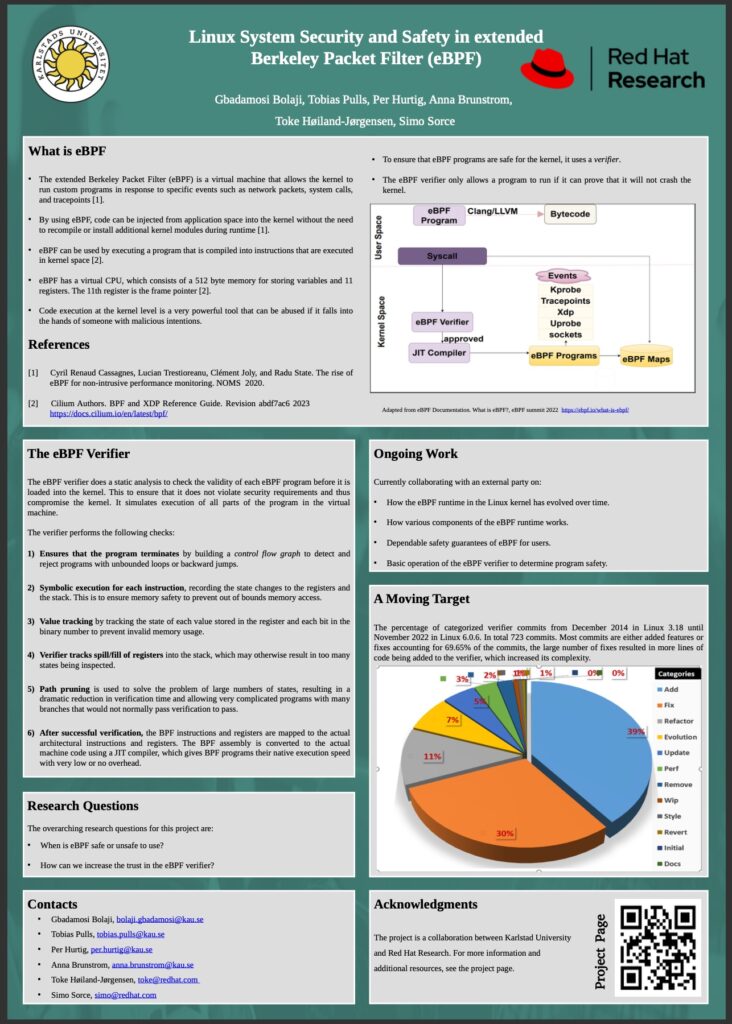
Security and safety of Linux systems in a BPF-powered hybrid user space/kernel world
Note: See the Building the next generation of programmable networking – powered by Linux project page for another project related to BPF usage in the Linux kernel.
Introduction
With the introduction of BPF into the Linux kernel, we are seeing a sea change in the traditional application model. With BPF it is now possible to execute parts of the application logic in kernel space, leading to a novel hybrid userspace/kernel model. This is an exciting development that brings with it many opportunities, but also some challenges especially in the area of security. We have recently seen an example of this around the “kernel lockdown” functionality in the kernel, which would disable BPF entirely in its “confidentiality” mode.
While exploring cryptographic signing of BPF programs as a possible way to reconcile kernel lockdown with loading BPF programs, it became clear that as BPF grows in popularity and gains new use cases, a blanket “trusted/untrusted” distinction is unlikely to be sufficient. Instead, we need a more granular approach, and to explore other aspects of BPF security. This new application model opens many interesting possibilities, but also new threats in the security landscape.
To address these issues, we seek to establish a research project that will look broadly at the various security issues related to BPF, the Linux kernel, and hybrid applications. The project builds on the existing research collaboration between Red Hat and Karlstad University around the topic of programmable networking using BPF, and seeks to draw on both Red Hat’s expertise in Linux kernel and BPF development, and Karlstad University’s expertise in academic security research.
Problems this project seeks to solve
This project aims to explore multiple areas related to security and safety of Linux systems including BPF components. The exact areas to be explored will be adjusted along the way, as participants explore the possibilities. Areas of interest at the time of writing this include:
- Defining a coherent threat model for Linux and BPF. BPF introduces a hybrid kernel/userspace application model, where parts of the application logic can run in the kernel address space using BPF. This means the kernel/userspace barrier is no longer the demarcation point between applications and (trusted) kernel code, which affects threat modelling for both applications and the kernel. This project aims to define a coherent model for this, as no such model exists today.
- Exploring the security guarantees offered by the BPF verifier. The BPF verifier performs static analysis at the byte code level for every BPF program loaded into the kernel. This is done to ensure that BPF programs are safe to run inside the kernel, by doing things like verifying memory accesses and preventing loops. However, there are potentially many other safety and/or security checks that the verifier could perform. This project aims to explore the limitations of the existing verifier checks and develop novel checks that can improve the guarantees of the BPF verifier, as well as to explore the attack surface presented by the verifier itself as it is processing BPF programs.
- Defining a framework for how to think about BPF and security. The hybrid kernel/userspace application model enabled by BPF is a departure from traditional application models, and requires new ways of thinking about application and system security. This includes both analysing the properties of applications that run BPF code in the kernel, but also using BPF as an additional security mechanism for constraining traditional userspace applications, as well as implementing subsets of kernel functionality in BPF. Developing a framework for thinking about BPF and security is an important contribution to the ecosystem.
- Analysing kernel resource constraint mechanisms in relation to BPF. Moving parts of the application logic into kernel space in BPF raises questions around resource allocation: for instance, can this facility be used to bypass resource constraints (such as CPU and memory allocations for a container), and how should resources be allocated for BPF programs shared between applications? At the same time, BPF can itself be a way to implement resource constraints, as seen in e.g., the cgroupv2 subsystem.
- Exploring memory safety issues for BPF code. The recent years have seen many new vulnerabilities related to memory safety and side channels. Running in kernel mode, BPF programs have the potential to be a new vector for these kinds of attacks. As such, analysing the susceptibility of BPF programs to memory side channel attacks, and exploring mitigations in the verifier or otherwise, is another potential focus for this project. The “memory safety” topic can also include exploring ways of selectively permitting memory writing for some BPF programs while restricting it for others, and how to distinguish between the two.
- Integrating BPF in safety-critical Linux applications. Recent times have seen an increasing interest in deploying Linux in safety-critical application scenarios, as seen by the ELISA project launched under the Linux Foundation umbrella in 2019. Exploring how BPF fits into such deployments is also a potential area of interest for this project.
- Exploring cryptographic signatures as a security mechanism for BPF programs. The kernel community has started to investigate the use of cryptographic signatures for BPF programs. While this work is already proceeding, it has possible implications for the topics outlined above, and so integrating this work is explicitly part of the project scope.
Project Poster