Masaryk University
The cooperation between Masaryk University and Red Hat Czech was established in 2007, just one year after the Red Hat Czech subsidiary was formed. Long-term cooperation with Red Hat happens on multiple levels and includes supervising bachelor‘s and master‘s theses focused on real projects, sponsoring PhD students and their open research projects, and teaching accredited courses led by experienced Red Hat associates.
Red Hat offers students the opportunity to pursue research activities and projects directly in their own open-source lab, which serves as the place to support common activities between Red Hat and the faculty.
UML
News
EU-funded cybersecurity consortium kicks off in Brno, Czech Republic
Authors Jaroslav Řezník, Principal Program Manager—Technical at Red HatViktor Malík, Senior Software Engineer at Red Hat Cybersecurity has become a critical focus of research in today's interconnected world, especially with the rise of cyberattacks posing a threat to...
Three researchers from the Faculty of Informatics involved in Red Hat Research were awarded with the 2021 “MUNI Innovation Award”
Masaryk University awarded the 2021 “MUNI Innovation Award” at its Business Research Forum on November 11, 2021. These new awards aim at individual students and employees whose outputs have been successfully implemented in practice, have helped improve products or services or have otherwise contributed to increasing the social relevance of Masaryk University’s research activities.
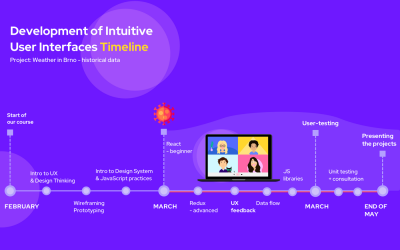
Teaching UX/UI at Masaryk University during the lockdown
In February 2020, four colleagues from Red Hat Brno decided to organize a full-semester course called Development of Intuitive User Interfaces at Faculty of Informatics, Masaryk University. How did they cope with the coronavirus crisis?
Open Days at Faculty of Informatics, Masaryk University
On February 6th, the Faculty of Informatics at Masaryk University opened its doors to the public. Open Days is a great opportunity for potential applicants for studies at the faculty.
Highlights in data-intensive science from Red Hat Research Day Europe
On January, 23, the day before Devconf.cz, the Research team organized its own academic conference, inviting a score of speakers from our university circles.
Related Projects
Title Summary Research Area CHESS: Cyber-security Excellence Hub in Estonia and South Moravia The Cyber-security Excellence Hub in Estonia and South Moravia (CHESS) brings together leading R&I institutions in both regions to build … Security, Privacy, Cryptography Side-channel attacks on embedded devices and smartcards This project focuses on several aspects of side-channel attacks on embedded devices and smartcards, utilizing timing, power-analysis and other side-channels. … Security, Privacy, Cryptography Sec-certs: Mining issued Common Criteria and FIPS140-2 certificates The security certification reports might be long but is also a trove of publicly available data about otherwise proprietary devices … Security, Privacy, Cryptography Verifying constant-time cryptographic algorithm implementations The aim of this project is to verify the timing side-channel resistance of cryptographic implementations. The project focuses on the constant time (and constant memory access) generic cryptographic implementations of selected cryptographic algorithms. T Security, Privacy, Cryptography Trusted Computing Ecosystem The project aims to study the TPM ecosystem as currently exists in deployed devices and software applications using it, establish the types of chips and their properties one can encounter, investigate the state of patching of known vulnerabilities like ROCA against Infineon’s TPM (CVE-2017-15361) or TPMFail against Intel’s fTPM (CVE-2019-11090) and STM’s TPM (CVE-2019-16863) and analyze a reliability of stored integrity measurements (PCRs) for remote attestation and disk encryption uses. Security, Privacy, Cryptography Authentication in public open-source repositories This project focuses on user authentication in public repositories containing open-source projects, which are then used by commercial companies (e.g. Red Hat) as a source for their internally maintained repositories. Security, Privacy, Cryptography Vega Project The Vega Project team at Red Hat came up with an idea to harness the power of Kubernetes to provide the next-generation open-source tool for high-performance computing. The project is way past the design phase, and the team is already working on the proof-of-concept implementation using Red Hat OpenShift Container Platform.