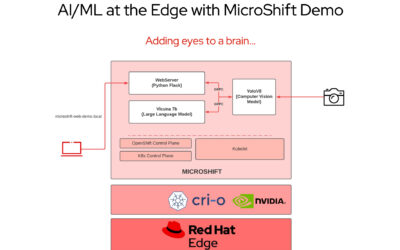
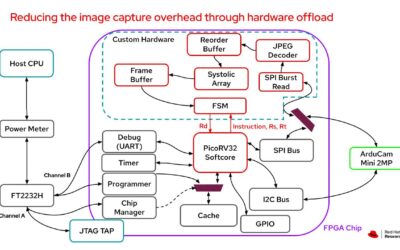
By Anastasia Braginsky
The 16th ACM International System and Storage Conference (SYSTOR), held June 5-7 in Haifa, Israel, featured five posters highlighting Red Hat-sponsored research projects that target challenges in cloud implementation strategy, storage performance, network observability, and AI/ML-enhanced cybersecurity analysis.
SYSTOR is a prestigious international conference held annually, aimed at the shared interests of academic and industrial researchers and practitioners. Out of the 22 posters accepted for the conference, these five introduced innovative work from either Red Hat engineers or academic teams sponsored by Red Hat.
CCO—Cloud Cost Optimizer
Adi Yehoshua and Ilya Kolchinsky, Red Hat; Assaf Schuster, Technion
The Cloud Cost Optimizer project is a collaboration between Technion and Red Hat Research. Its goal is to design and implement a scalable multicloud cost optimizer capable of calculating the best scheme for deploying a given arbitrary complex workload over a public/hybrid cloud, thus reducing the monetary cost. A fully functional version of CCO is currently available for use, with extensions and improvements already underway.
To learn more, visit the CCO project page or read the article “Meet CCO: a scalable multicloud optimizer for complex workloads” in the May 2023 issue of the Red Hat Research Quarterly.
Efficient hashing of sparse virtual disks
Nir Soffer, IBM; Erez Waisbard, CyberArk
Verifying the integrity of a file is a fundamental operation in file transfer. We introduce blkhash: a novel hash algorithm optimized for disk images that is up to four orders of magnitude faster than commonly used tools. We implemented a new command-line tool and library that can be used in the virtualization space for verifying storage management operations. Our approach can significantly contribute to use cases including very fast computing of virtual disk hash value in software-defined storage and verifying an entire disk image content as part of a supply chain integrity verification or in the context of confidential computing. Nir is a former Red Hatter, now at IBM. Anastasia Braginsky from Red Hat Research Israel collaborated with him on the poster submission.
To learn more, visit the Blkhash project repository.
On latency awareness with delayed hits
Gil Einziger, Nadav Keren, and Gabriel Scalosub, Ben Gurion University
We consider a new locality pattern in the form of burstiness to improve cache effectiveness in workflows where items are requested in possibly infrequent yet costly batches. Adding a cache that handles only bursty items to existing state-of-the-art algorithms shows a significant improvement in overall average time per query. This poster reports on work from the project “Advance proactive caching for heterogeneous storage systems,” which aims to improve the performance of distributed storage systems such as Ceph and NooBaa by developing novel caching frameworks that take into account request heterogeneity and perform proactive caching decisions.
To learn more, visit the “Advance proactive caching for heterogeneous storage systems” project page.
Next-generation security entity linkage harnessing the power of knowledge graphs and large language models
Daniel Alfasi and Tal Shapira, Reichman University; Anat Bremler-Barr, Tel Aviv University
With the continuous increase in reported Common Vulnerabilities and Exposures (CVEs), security teams are overwhelmed by vast amounts of data that is often analyzed manually, leading to a slow and inefficient process. Establishing connections across multiple security entity databases, including CVEs, Common Weakness Enumeration (CWEs), and Common Attack Pattern Enumeration and Classification (CAPECs), is essential to addressing cybersecurity threats effectively. We introduce a new approach leveraging the RotatE knowledge graph embedding model, initialized with embeddings from the Ada language model developed by OpenAI. Additionally, we extend this approach by initializing the embeddings for the relations.
Learn more about the project “Common Vulnerabilities and Exposures (CVEs) mining and prediction,” the Red Hat Research project from which this work is drawn, on its project page.
Smart network observability—connection tracking
Ronen Schaffer, Eran Raichstein, and Kalman Meth, IBM Research; Joel Takvorian and Julien Pinsonneau, Red Hat
Flow Logs Pipeline (FLP) is an observability tool that consumes flow logs from various inputs, transforms them, and exports logs to Loki and/or time series metrics to Prometheus. While flow logs encompass a lot of valuable data, the resolution of flow logs is often too low for observing the network effectively. We are often interested in observing it from a higher resolution— the resolution of connections. In this work, we introduce a new processing stage in FLP that allows aggregating flow logs from the same connection, or connection tracking.
We are excited that many Red Hat associates actively participated in SYSTOR, and we are proud to have been a platinum sponsor of this important conference. By participating in SYSTOR 2023, we continue to foster innovation and collaboration in the field of systems and storage.