Fuzzing Device Emulation in QEMU
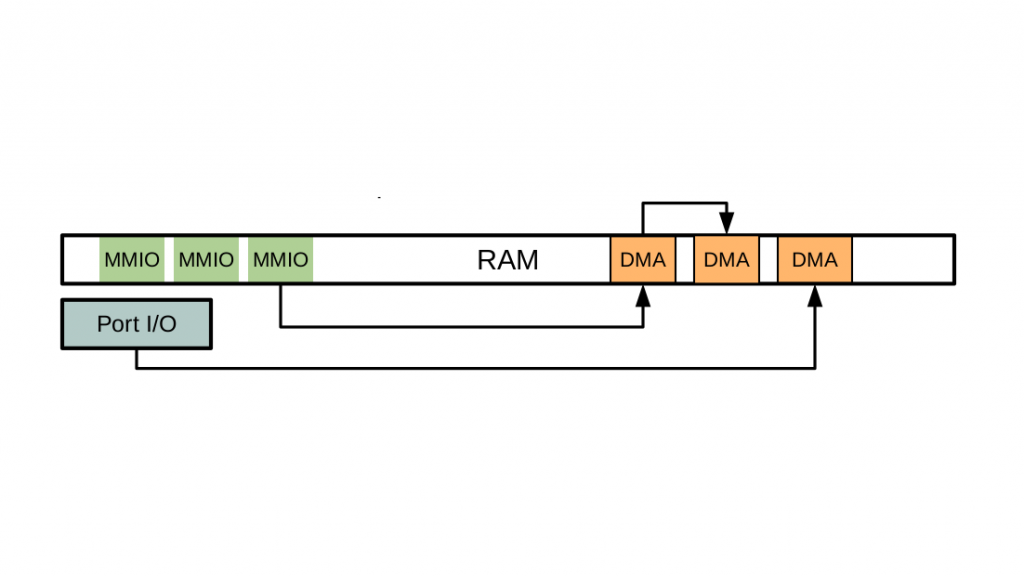
Hypervisors—the software that allows a computer to simulate multiple virtual computers—form the backbone of cloud computing. Because they are both ubiquitous and essential, they are security-critical applications that make attractive targets for potential attackers. Past vulnerabilities demonstrate that implementations of virtual devices are the most common site for security bugs in hypervisors. To address this problem, we have developed a novel method for fuzzing virtual devices and implemented it for the popular open source QEMU hypervisor. Our fuzzer combined a standard coverage-guided strategy with further guidance based on hypervisor-specific behaviors. It guarantees reproducible input execution and can, optionally, take advantage of existing virtual device test cases. In our evaluation, we found and reported previously unknown bugs in devices such as serial and virtio-net, ranging from memory corruptions to denial-of-service vulnerabilities. Our evaluation demonstrated that combining well known coverage guidance techniques with domain-specific feedback results in promising fuzzer performance, even for complex targets such as hypervisors.
This project was jointly supported by Red Hat, BU, and the Google Summer of Code 2019. Research continues as part of the Red Hat Collaboratory.
For more information on this project and the unique partnership that produced it, please see the website of the Red Hat Collaboratory at Boston University as well as the article by Alex Bulekov in Red Hat Research Quarterly, Volume 2, Issue 1.