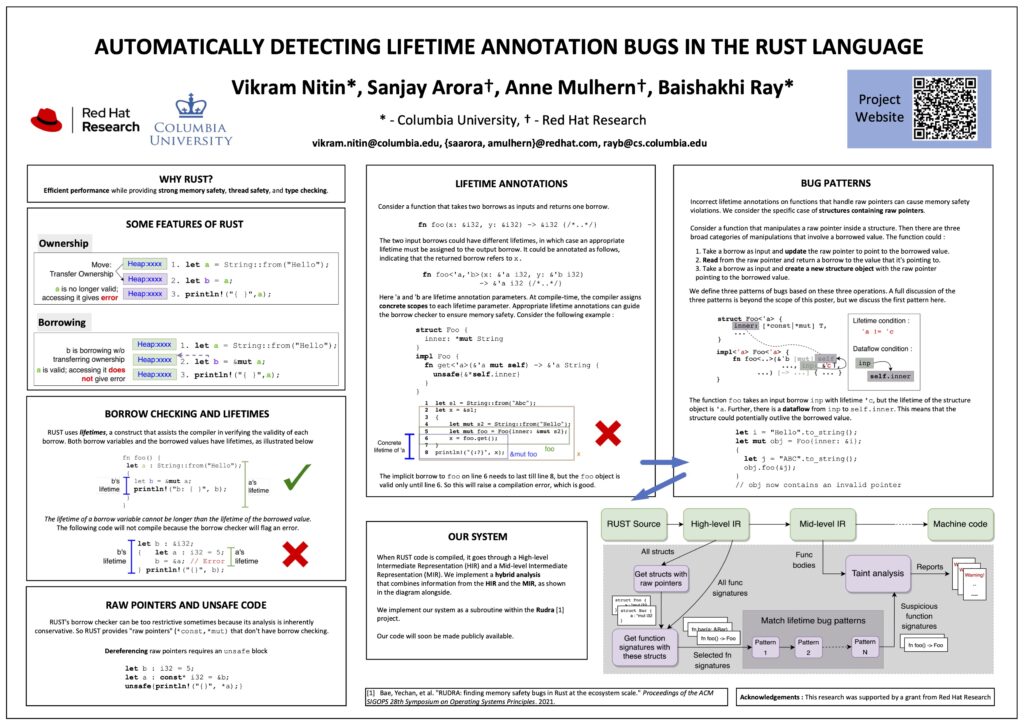
Automated detection of memory safety vulnerabilities in Rust
In comparison to C, the Rust language provides significant memory safety guarantees through its concept of lifetimes and its borrow-checker. However, Rust has an “unsafe” keyword which suspends some of the compiler’s safety checks within a specified code block. Such unsafe code destroys the guarantees of a program written in pure Rust, and it becomes the responsibility of the developers to ensure the memory safety of the unsafe code. For example, a function that internally uses the unsafe code should still have the same memory safety guarantees as a function written in pure Rust. If the function is not implemented correctly, then those who use this function may write code that is vulnerable to memory safety errors, even though the code that they write is pure Rust.
In this presentation, we explain different types of memory safety vulnerabilities that can arise in Rust programs and present our ongoing work on automated detection of these vulnerabilities.
Watch: Research Days 2022: Preventing Rust Programs From Becoming C Programs (May 2022)
Project Poster